Isolated application VMs on NixOS with appvm
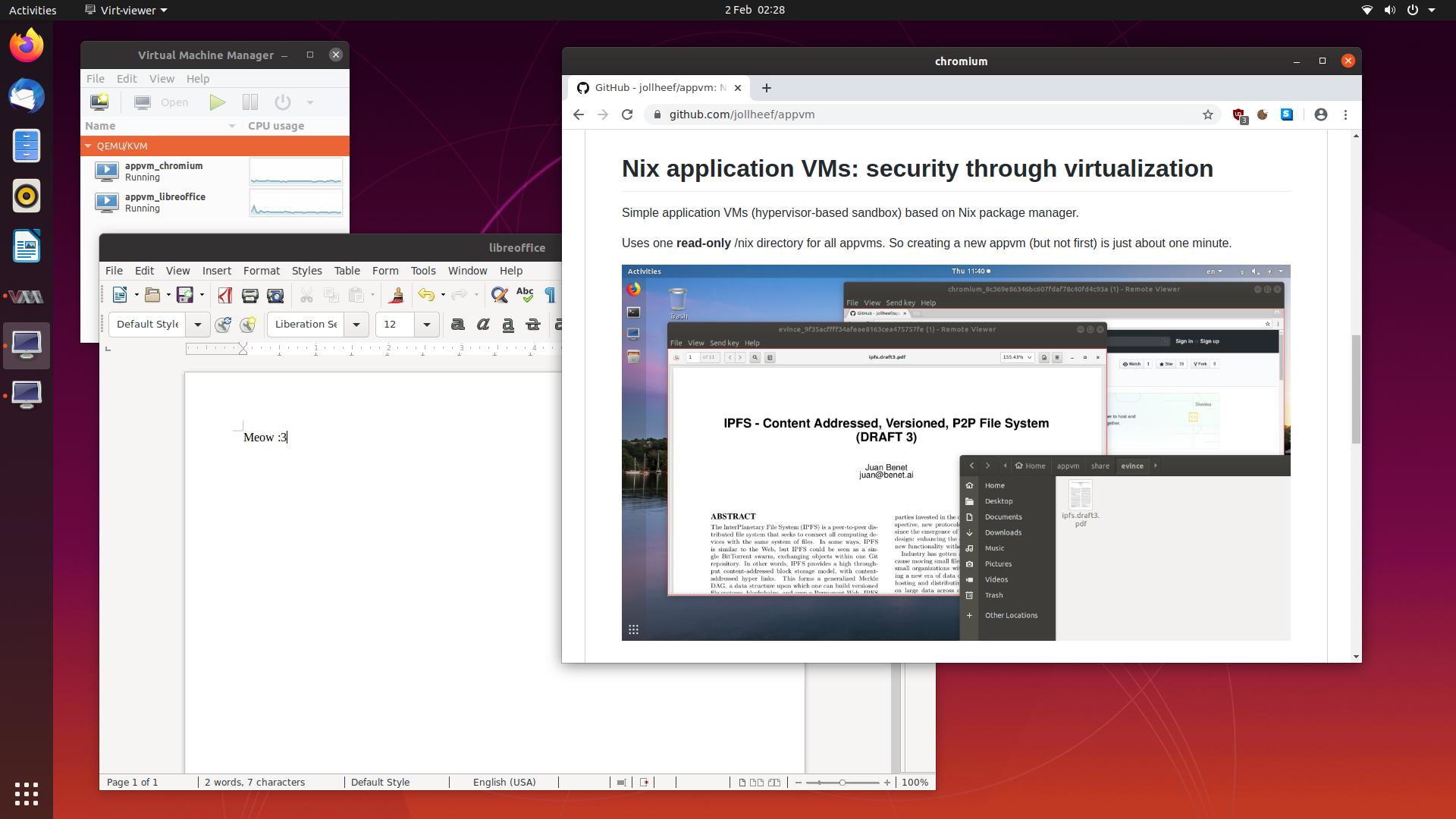
Running applications inside a virtual machine could possibly be the most secure sandboxing approach. appvm is a small Go program developed by jollheef and cab404 to run apps seamlessly inside a virtual machine, similar to Quebes OS.
To configure permissions and install appvm, paste following code to your system configuration and enable it. Replace user onny with the username of your current running user.
services.virtualisation.appvm = {
enable = true;
user = "onny";
};Now start the app with following command
appvm start chromiumIf everything worked, the virtual machine including the app should start like this
Note that appvm is an experimental project with no guarantee on stability or security.
Currently the app and module is not yet available in a stable repository but should hopefully land in NixOS 22.05 or later.